Update 2023-06: Cyrill Künzi’s↗ post Hacking my “smart” toothbrush↗ goes way beyond mine. He found that a password is needed to reset the counter. Just a few days later, Aaron Christophel↗ cracked the algorithm by dumping the firmware and reversing the code↗.
But Why? #
Somewhere in 2020, I bought an electric toothbrush. The exact model would be Philips Sonicare ProtectiveClean 4500. It’s sometimes referred to as HX6830. After using it for a few weeks, it started a weird behavior. Not always but a few times it would randomly stop while brushing, vibrate in a strange pattern and then start again. Since it’s a toothbrush with only two buttons it didn’t come with a manual. After searching the web I found the manual↗. It clearly mentions a “Brush head replacement reminder”.
 |  |
The weird vibrating pattern according to the manual meant that the brush head was worn out. But I only had this thing for about 6 weeks. That can’t be true. The brush head looked absolutely fine. And besides that 4 new brush heads cost about 25$. That sounds to me like planned obsolescence↗.
Quick side note: You can simply follow the manual and deactivate this reminder. The brush won’t bother you anymore. But for me, the part of my brain which likes to break stuff was already hooked enough.
Inspecting the Brush #
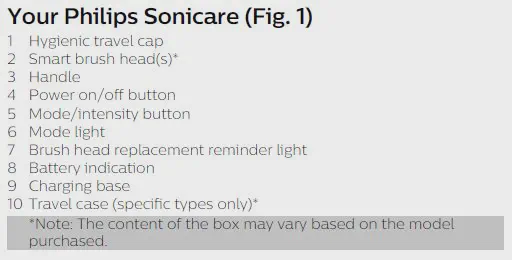
The brush itself has two buttons and four led lights. One button turns the device on, and the other switches the mode between “clean” and “white”. The two LEDs at the bottom tell you to change the brush head as well as when to charge the device.

Indeed the “Change brush head” led was already blinking at me. At this point, I was wondering how the brush knows the runtime of a brush head. When taking the head off, there was some sort of tag, as well as the reader, was clearly visible.
 |  |
Inspecting the Tag #
This tag could function in multiple ways:
- The tag inside the head has a serial number and the brush itself keeps track of the used minutes alongside the serial numbers
- The brush writes the elapsed time to the tag inside the head
- Both at the same time
The second option could easily be ruled out if I had a second brush which I don’t have. It was time to get my Android phone to inspect the tag. With NFC Tools↗ I was able to read some data when holding the head against the reader of my phone. So it’s an NFC tag.
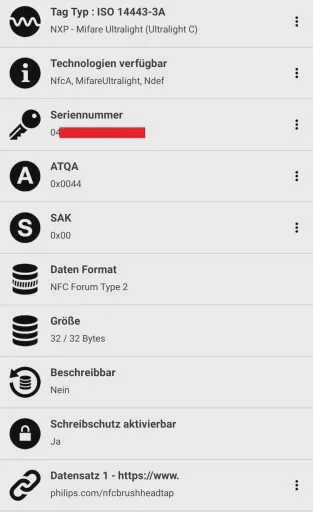
The tag type is a MIFARE Ultralight C. I knew from experiments some time ago that MIFARE Classic tags are really easy to hack. Unfortunately Ultralight and Ultralight C are not. Fun fact: MIFARE (NXP) is owned by Philips. The URL it redirects to is philips.com/nfcbrushheadtap↗, which is the page for buying new heads.
I then googled if somebody had already done some research on this problem. Indeed I found a blog post↗ about the main chip as well as the NFC driver. Unfortunately, this blogger didn’t go any further than inspecting the hardware. The brush in the blog post is also not the exact model I have. In the comments, a user mentions that when he takes the head to another brush it still blinks to renew the head. So there is some writing to the head involved.
Since I didn’t own any USB NFC readers/writes I ordered a ACR122U NFC reader and some NFC tags from China. The NFC Tools Wiki mentions that this chip does not have full functionality. I searched for more compatible chips but could not find any. So I went with what I found.
This concludes the first part of this journey. Since I don’t want to waste a perfectly functioning toothbrush, I’ll continue once the battery inside the brush loses enough capacity to make the brush obsolete. As mentioned in the beginning, the code is now cracked and I’ll not continue this series.